About me
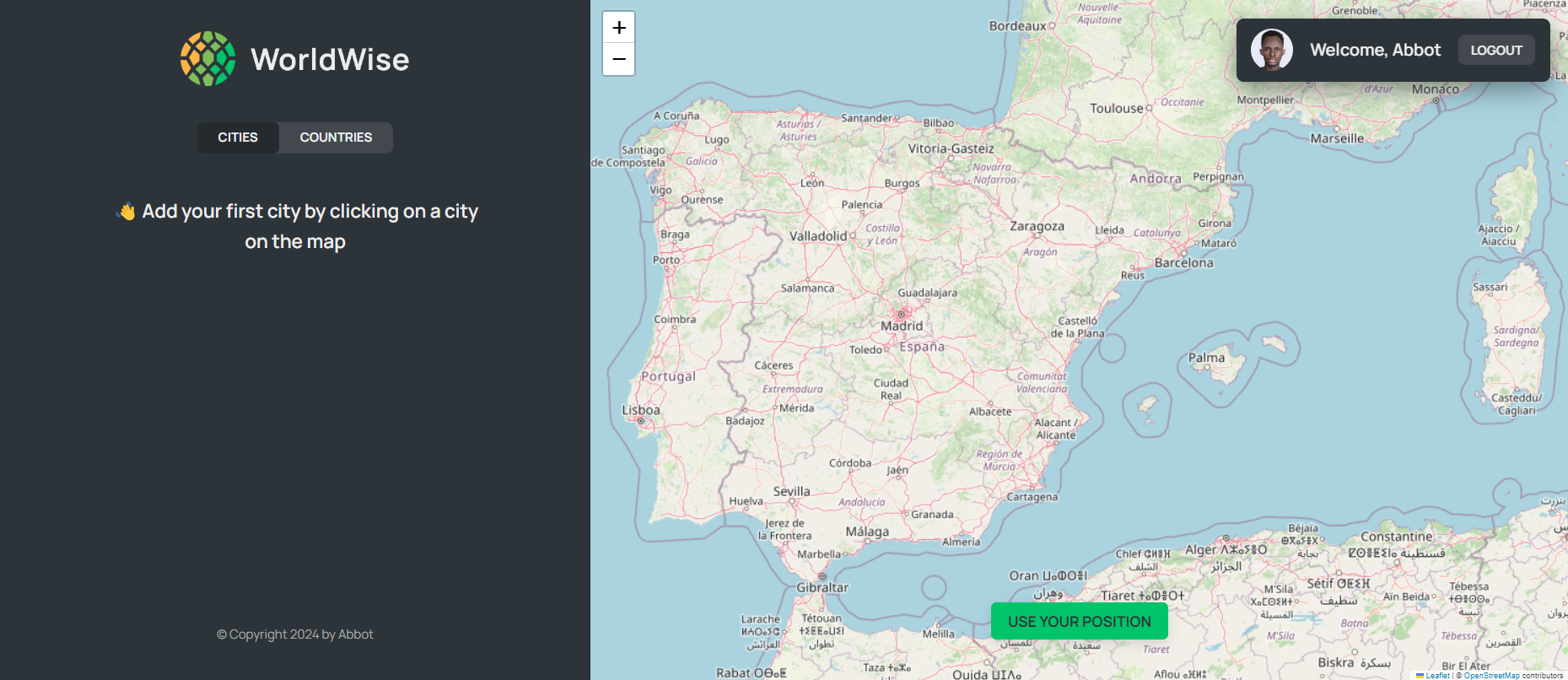
I'm a student in Boston, pursuing a double major in computer science and cybersecurity. My passion for technology has driven me to embark on a self-taught journey in software engineering, taking me from zero to where I am today. Along the way, I've worked on a variety of projects, spanning from front-end to full-stack development. Exposure to both computer science and cybersecurity practices has fueled my desire to continuously acquire new skills. I've enrolled in courses covering topics like Practical Ethical Hacking, Open-Source Intelligence, Windows and Linux Privilege Escalation, and External Penetration Testing.
While having such a diverse skill set has presented me with the challenge of choosing a specialization, my approach to the digital world is to learn as many skills as possible, one step at a time. All the coding projects in my portfolio are meticulously crafted from initial planning and design to problem-solving, reflecting my commitment to hands-on learning and development.
Certifications
Professional Certifications: ISC2(CC), Oracle Data Management (Certified Foundations Associate), AWS Cloud Practitioner (In-progress), Practical Network Penetration Testing (PNPT - In progress)
General Certificates: API Security Fundamentals, API Penetration Testing, Practical Ethical Hacking (TCM Security), External Penetration Testing (TCM Security), Azure Administration, Software Architecture Foundations
What I do
-
Front End Development
Crafting intuitive and responsive user interfaces using popular frontend frameworks.
-
Backend Development
Building robust and scalable server-side solutions to support seamless application performance.
-
Web Application Penetration Testing
Identifying and mitigating vulnerabilities in web applications to ensure security and resilience of applications.
-
Network Penetration Testing
Assessing network security to protect against potential threats and unauthorized access. (In windows and azure active directory environments)
-
API Penetration Testing
Ensuring the security of APIs and providing mitigation strategies for common API vulnerabilities.
-
Bug Bounty Hunting
Actively participating in bug bounty programs on HackerOne and bug crowd.